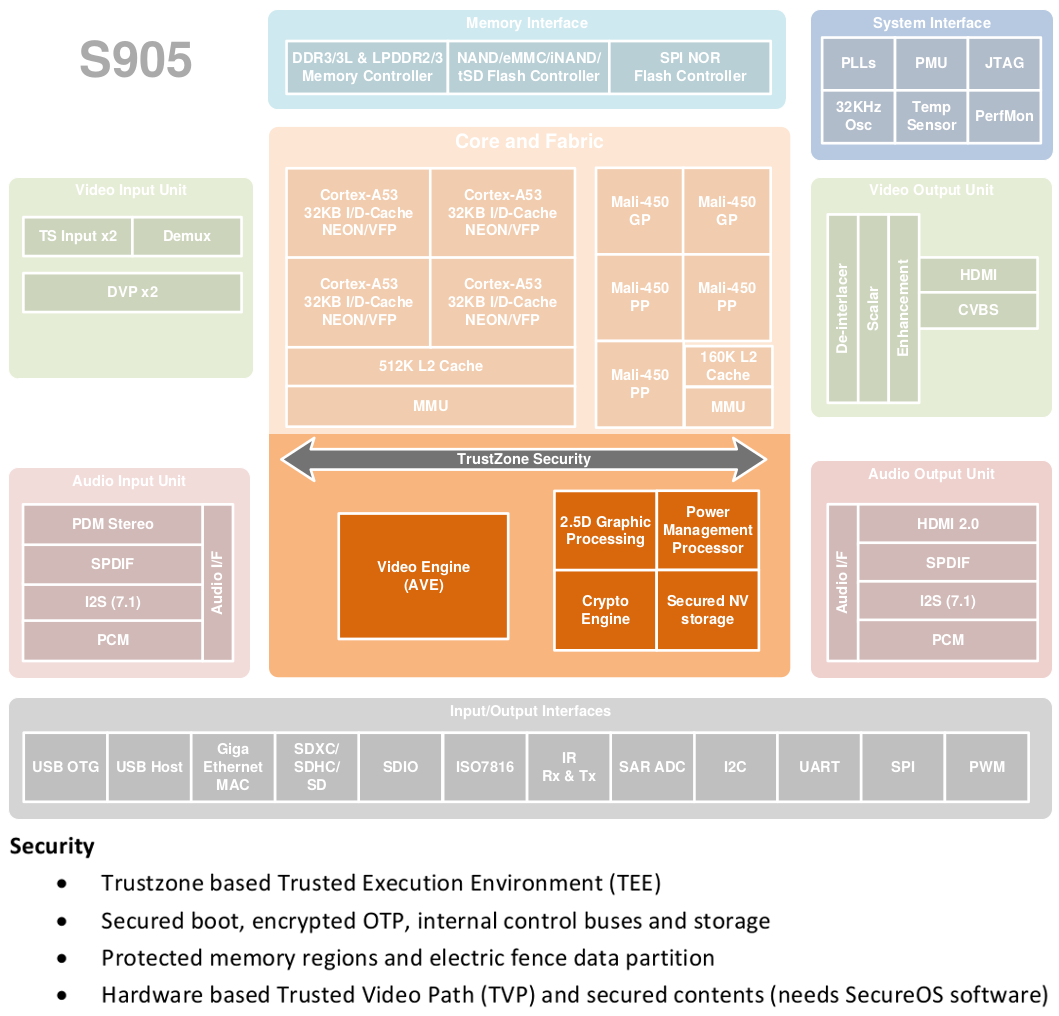
exynos8890-bootrom-dump : dump Exynos 8890 bootROM from Samsung Galaxy S7
Posted on Mon 15 June 2020 in Tool • Tagged with arm, exynos, samsung, bootrom, trustzone, exploit
This post introduces a tool to dump Samsung Galaxy S7 bootROM using known and fixed security vulnerabilities in Trustzone.
The source code is available on GitHub.
Procedure
We use a Galaxy S7 phone, with ADB access and root privileges.
BootROM code is at address 0x0, in Secure world. The TEE …
Continue reading